NIS Master Server Config
NIS maps are located in /var/yp/domainname directory(where domainname is the name of the NIS domain). There are two files (.pag and .dir files) for each map in this directory. Eg.
/var/yp/training/hosts.byname.pag file
/var/yp/training/hosts.byname.dir file
/var/yp/training/hosts.byaddr.pag file
/var/yp/training/hosts.byaddr.dir file
The syntax for the NIS map is map.key.pag and map.key.dir
Ypcat [-k] mname -- To retrieve values from NIS name service map, mname can be either a
map name or a map nickname
# ypcat hosts
localhost 127.0.0.1 localhost
sysprint 192.168.30.70 sysprint
sys44 192.168.30.44 sys44 loghost
ypmatch [-k] value mname -- Prints values associated with one or more keys from the NIS
name services map specified by the mname argument.
# ypmatch sys44 hosts
sys44: 192.168.30.44 sys44 loghost
# ypmatch usera passwd
usera: usera:LojyTdiQev5i:3001:10::/export/home/usera:/bin/ksh
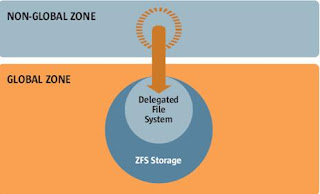
NIS Domain Contains
One NIS Master Server
NIS Slave Servers (Optional)
NIS Clients
The NIS Master Server
Contains the original /etc/ASCII files used to build the NIS maps
Contains the NIS maps generated from the ASCII files
Provides a single point-of control for the entire NIS domain
NIS Slave Servers
Do not contain the original /etc/ASCII files
Contains copied of the NIS maps copied from the NIS Master Server
Provides a a backup repository for NIS map information
Provides redundancy in case of server failure
Provides load sharing on large networks
NIS Clients
Do not contain original /etc/ASCII files
Do not contain any NIS maps
Bind to the master server or to a Slave Server to obtain access to the administrative file information contained in that server’s NIS maps
Dynamically rebind to another server in case of server failure
Make all appropriate system calls aware of NIS
NIS Processes
The main daemons involved in the running of an NIS domain are
The ypserv daemon -- Responds to client information requests
The ypbind daemon -- Client to server binding
The rpc.yppasswd daemon -- Password change update in master server
The ypxfrd daemon -- Push the map to slave servers (sync)
The rpc.ypupdated domain -- Update NIS maps using the config stored in /var/yp/updates
The NIS Slave Server contains upserv and ypbind daemon
The NIS Clients contains only ypbind daemon
The three most common search orders are
Search files and then NIS
Search NIS and then files
Forward hosts lookup requests from NIS to DNS
Introducing NIS Security
The /var/yp/securenets file to restrict access to a single host or to a subnetwork, and using the passwd.adjunct file to limit access to the password information across the network.
The /var/yp/securenets File
If exist on an NIS server, the server only answers queries or supplies maps to hosts and networks whose IP Address exist in the file. The server must be part of the subnet to access itself.
# cat /var/yp/securenets
# Two methods of giving access to a system. Using the netmask followed by the IP Address
# or host keyword followed by the IP Address
host 127.0.0.1
255.255.255.0 150.10.1.0
host 13.13.14.1
host 13.13.14.2
If you modify entries in the /var/yp/securenets file. You must kill and restart the ypserv and ypxfrd daemons.
# /usr/lib/netsvc/yp/ypstop (or) ypstart
The passwd.adjunct File
Encrypted password are normally hidden from the user in the /etc/shadow file. With the default NIS configuration, however the encrypted password string is shown as part of passwd maps. This file prevents unauthorized users from seeing the encrypted passwords.
# ypmatch –k usera passwd
usera: usera:LojyTdiQev512:3001:10:/export/home/usera:/bin/ksh
The passwd.adjunct file contains the account name preceded by ## in the password field. Subsequent attempts to gain account ino, using the ypcat or ypmatch commands, returnds the password entry from the passwd adjunct file.
# ypmatch –k usera passwd
usera: usera:##usera:3001:10:/export/home/usera:/bin/ksh
Configuring NIS Domain
To locate the source file in another directory, modify the /var/yp/Makefile file:
Change the DIR=/etc line to DIR=Your choice
Change the PWDIR=/etc line to PWDIR=/your-choice
Before you make any modification to the /var/yp/Makefile, save a copy of the original Makefile file.
The NIS configuration script /usr/sbin/ypinit and the make utility generate NIS maps. The ypinit command reads the Makefile for source file locations, and converts ASCII scource files into NIS maps.The /etc/defaultdomain file sets the NIS domain name during system boot.
Important files on the NIS Master (Part 1) -- hosts, passwd & shadow
Important files on the NIS Master (Part 2)
The /var/yp/domainname directory is the repository for the NIS maps created by the ypinit script.
The /var/yp/binding/domainname directory contains the ypservers file where the names of NIS Master server and NIS Slave server are stored.
Important files on the NIS Master (Part 3) -- The /usr/netsvc/yp directory contains the ypstop and ypstart commands that stop and start NIS services respectively
# /usr/sbin/ypinit –m -- This command prompts for a list of other machies to become NIS
slave servers.
Configuring the NIS Master Server
Core, End User or Developer software configuration cluster do not have all necessary files in the /usr/lib/netsvc/yp directory to allow a host to function as an NIS server.
1. Copy the /etc/nsswitch.nis file to the /etc/nsswitch.conf file. If necessary, modify the file
2. Enter the domainname command to set the local NIS domain
# domainname classroom.central.sun.com
3. Create an /etc/defaultdomain file with the domain name
4. If the files do not already exist, use the touch command to create zero-length files.
/etc/ethers, /etc/bootparams, /etc/locale, /etc/timezone, /etc/netgroup and /etc/netmasks.
These files are necessary for the creation of the complete set of NIS maps.
5. Install and update Makefile file in the /var/yp directory.
6. Create or populate the /etc/locale file, and make an entry for each domain on your network
using the following format
domainname locale eg. Classroom.central.sun.com en_us
7. Initialize the master server by using the local /etc files
# ypinit –m -- Provide slave server names and Ctrl+D to save the details. Press n for
“Terminate it on the first fatal error”
Note: If you have to restart the ypinit program, You are prompted to destroy the
/var/yp/domainname directory. Answer Y
8. # /usr/lib/netsvc/yp/ypstart
Testing the NIS Service
$ ypcat hosts -- Prints value from an NIS map
# ypmatch sys41 localhost hosts
192.168.30.41 sys41
127.0.0.1 localhost loghost
$ ypwhich -- To identify the master server
sys41
Configure the NIS Client
1. Copy the /etc/nsswitch.nis file to the /etc/nsswitch.conf file
2. Edit the /etc/inet/hosts file to ensure NIS master and slave servers have been defined.
3. # domainname domainname -- To set the local NIS domain
4. Create and populate the /etc/defaultdomain file with the domain name
5. # ypinit –c -- To initialize the system as an NIS client
6. Enter the names of the NIS Master and all Slave Servers
7. # /usr/lib/netsvc/yp/ypstart
8. # ypwhich –m -- To test the functionality
Configuring NIS Slave Server
Follow the client configuration steps and perform the below command
# ypinit –s master -- Command to initialize the system as an NIS slave server. Where master is the name of the NIS master. Start the service and test the functionality
Updating the NIS Map
1. Updates the text files in your source directory (typically /etc, unless it was changed in the Makefile file)
2. # cd /var/yp
3. # /usr/ccs/bin/make -- Refresh the NIS database maps using the make utility
Updating NIS Password Map
If the NIS master is running the rpc.yppasswdd daemon, any client system can update the NIS password map by using the yppasswd or passwd commands.
1. Run the rpc.yppasswdd daemon on the NIS master server
# /usr/lib/netsvc/yp/rpc.yppassed /$PWDIR/passwd –m passwd
Updating the NIS Slave Server Map
The following steps manually update the NIS timezone map on the master server and propagate all maps to the slave servers
1. Edit the source file on the NIS Master
# vi /etc/timezone
2. Remake and push the NIS maps to slave servers
# cd /var/yp; /usr/ccs/bin/make
3. If the push fails. Manually pull only the timezone map from the master server by
performing the below command in Slave server
# /usr/lib/netsvc/yp/ypxfr timezone.byname
# ypinit –s nis_master -- To pull all of the maps at once
Sometimes maps fail to propagate, and you must manually use the ypxfr command to retrieve new map information. You can use shell scripts to run cron jobs for automatic update. The Solaris OE provides several template scripts in the /usr/lib/netsvc/yp directory that you can use and modify to meet your local site requirement.
ypxfr_lperhour script -- To sync NIS Slave Servers passwd map
ypxfr_lperday script -- To sync NIS Slave Servers NIS maps for the group, protocols,
networks, services, and upservers keys.
Ypxfr_2perday script -- To sync NIS Slave servers nIS maps for the hosts, ethers, netfroups keys, and mail aliases.
Quick Reference
# domainname digit.com -- Create domain name
# domainname > /etc/defaultdomain -- Creating domainname file
# cp /etc/nsswitch.nis /etc/nsswitch.conf
# /var/yp/Makefie -- Config file
Makefile 4 parts
1 – Declaration
2 – Details of centralization
3 – Coding for mapping
4 – Declaration of original path
# cd /var/yp
# ypinit –m -- Initializing the master server
# ypinit –s -- Initializing the slave server
# ypinit –c -- Initializing the client
Ctrl+D -- To save the file
Is this correct? [y/n] y
Non fatal error [y/n] n
If there is any error follow the below procedure
# cd /etc
# touch ethers bootparams netgroup netmasks timezone
# cd /var/yp
# ypinit –m
# /usr/lib/netsvc/yp/ypstart -- To start the daemons
# ypwhich -- Shows the map server details
Solaris
# ypwhich –m -- Full details of map
A directory will be created with domain name
# cd /var/yp/digit.com -- Contains all config file with .pag & .dir extensions
# ypcat
to read the file
# ypcat –k passwd -- With arguments print keys as well as values
# ypmatch –k root passwd